CMMC
Cybersecurity Maturity Model Certification (CMMC) Primer and Estimated Costs
CMMC (Cybersecurity Maturity Model Certification) is the Department of Defense’s (DoD) newest verification mechanism designed to ensure that cybersecurity controls and processes adequately protect Controlled Unclassified Information (CUI) that resides on Defense Industrial Base (DIB) systems and networks.
The Office of the Undersecretary of Defense for Acquisition and Sustainment (OUSD (A&S)) started the process of creating the CMMC in March 2019, the finalization of CMMC v1.0 being issued in January 2020.
The Department of Defense created a requirement for all organizations in the defense supply chain contracting with the government to achieve the appropriate level of Cybersecurity Maturity Model Certification. Organizations in the defense supply chain achieve the appropriate CMMC level through assessment by a neutral and properly accredited third party entity. This entity assesses an organization’s cybersecurity maturity against criteria defined in the CMMC standard.
The CMMC-Accreditation Body (CMMC-AB) is responsible for developing a scalable and extensive partner-centric training and educational model to effectively equip professionals, students and other stakeholders within the CMMC ecosystem. The CMMC-AB will, as part of its strategy, certify Licensed Partner Publishers (LPP) to develop learning content and Licensed Training Providers (LTP) to train stakeholders for certification or other purposes.
Individuals seeking certification by CMMC-AB as CMMC Certified Professionals (CP) or Certified Assessors (CA) must successfully complete a training program delivered by a LTP and pass a proctored examination prior to receiving certification to prepare for or conduct assessments. The CMMC-AB will license/accredit assessors to perform formal assessments under the CMMC once they satisfactorily complete the training, examination and certification requirements.
Assessors will affiliate with CMMC Third Party Assessment Organizations (C3PAOs). The C3PAOs serve as the interface between the Organizations Seeking Certification (OSCs), the Assessment and the CMMC-AB.
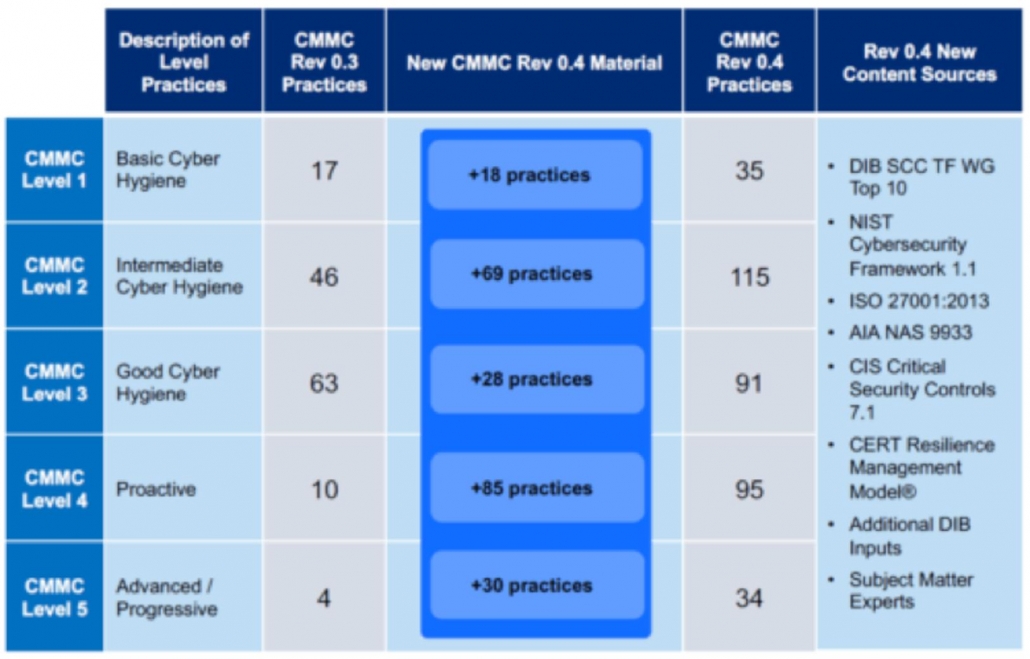
CMMC has five levels of certification. 17 domains are assessed even at the most basic level.
The Domains have seventeen (17) sections listed below:
- Access Control
- Asset Management
- Audit and Accountability
- Awareness and Training
- Configuration Management
- Identification and Authentication
- Incident Response
- Maintenance
- Media Protection
- Personnel Security
- Physical Security
- Recovery
- Risk Management
- Security Assessment
- Situational Awareness
- Systems and Communications Protection
- System and Information Integrity
Each level of CMMC maturity has increasing expectations:
- CMMC Level 1: 17 Controls.
- CMMC Level 2: 72 Controls (includes Level 1 controls)
- CMMC Level 3: 130 Controls (includes Level 2 controls)
- CMMC Level 4: 156 Controls (includes Level 3 controls)
- CMMC Level 5: 171 Controls (includes Level 4 controls)
Each of the levels is described in more detail below:
Level 1
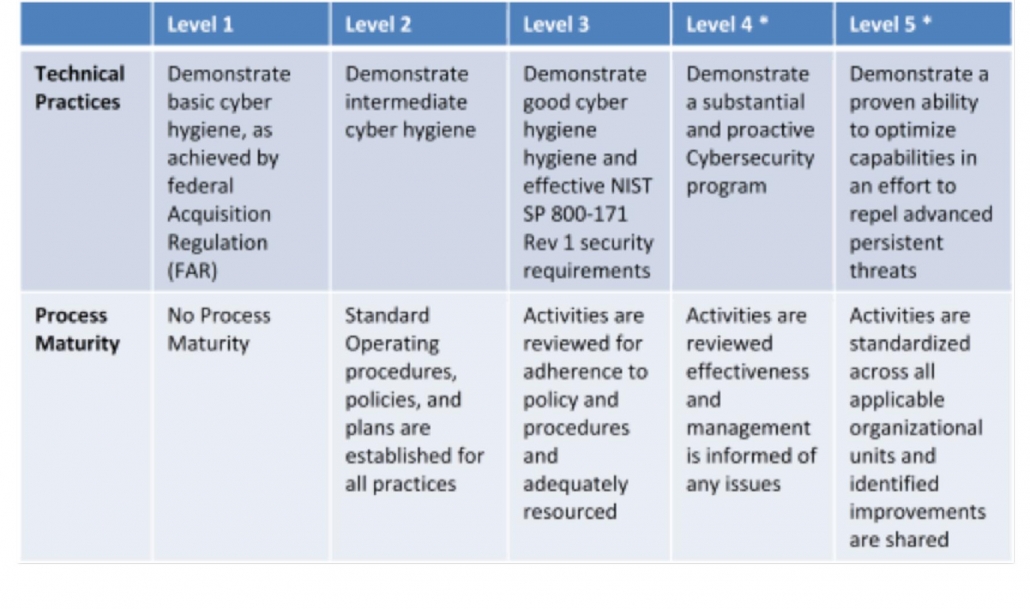
CMMC Level 1 focuses on basic cyber hygiene and consists of the safeguarding requirements specified in 48 CFR 52.204-21. The Level 1 practices establish a foundation for the higher levels of the model and must be completed by all certified organizations. Not every domain within CMMC has Level 1 practices. At both this level and Level 2 organizations may be provided with FCI. FCI is information not intended for public release. It is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government. FCI does not include information provided by the Government to the public. While practices are expected to be performed, process maturity is not addressed at CMMC Level 1 and therefore a CMMC Level 1 organization may have limited or inconsistent cybersecurity maturity processes.
Level 2
CMMC Level 2 focuses on intermediate cyber hygiene creating a maturity-based progression for organizations to step from Level 1 to 3. This more advanced set of practices gives the organization greater ability to both protect and sustain their assets against more cyber threats compared to Level 1. CMMC Level 2 also introduces the process maturity dimension of the model. At CMMC Level 2 an organization is expected to establish and document standard operating procedures, policies and strategic plans to guide the implementation of their cybersecurity program.
Level 3
An organization assessed at CMMC Level 3 will have demonstrated good cyber hygiene and effective implementation of controls that meet the security requirements of NIST SP 800-171 Rev 1. Organizations that require access to Controlled Unclassified Information (CUI) and/or generate CUI should achieve CMMC Level 3. CMMC Level 3 indicates a basic ability to protect and sustain an organization’s assets and CUI; however, at CMMC Level 3 organizations will have challenges defending against advanced persistent threats (APTs). Note that organizations subject to DFARS clause 252.204-7012 will have to meet additional requirements such as incident reporting. For process maturity a CMMC Level 3 organization is expected to adequately resource activities and review adherence to policy and procedures demonstrating management of practice implementation.
Level 4
At CMMC Level 4 an organization has a substantial and proactive cybersecurity program. The organization has the capability to adapt their protection and sustainment activities to address the changing tactics, techniques and procedures (TTPs) in use by APTs. For process maturity a CMMC Level 4 organization is expected to review and document activities for effectiveness and inform high-level management of any issues.
Level 5
At CMMC Level 5 an organization has an advanced or progressive cybersecurity program with a demonstrated ability to optimize their cybersecurity capabilities. The organization has the capability to optimize their cybersecurity capabilities in an effort to repel APTs. For process maturity a CMMC Level 5 organization is expected to ensure that process implementation has been standardized across the organization.
How Much Will CMMC Certification Cost?
For most organizations there are likely to be three primary costs to getting CMMC certified:
- Soft costs to prepare for the audit (e.g., internal resourcing or external consulting costs)
- Hard costs to prepare for the audit (e.g., expenditures to achieve a particular requirement such as a SIEM or two-factor authentication)
- Hard costs for the CMMC Audit itself (e.g., the cost for the Certified Auditor, which potentially will be an “allowable expense”)
Soft costs for getting prepared for the audit
Your actual costs will depend on a number of factors, including but not limited to the maturity of your current NIST SP 800-171 program, the size of your organization, whether you require external support, how many locations are involved, the CMMC Level you’re looking to achieve and the scope of your Controlled Unclassified Information (CUI). CUI scope is how many geographic locations, systems, databases, applications and networks store, process or transit CUI. To simplify, let’s break the above into two buckets and assume CMMC Level 3, which is likely to be the most common target:
- Organizations that have a reasonably mature SP 800-171 compliant environment
- Consulting Costs: You will likely want to employ a CMMC Gap Assessment (may be called a Readiness Assessment). For a typical 250-person engineering/manufacturing firm with multiple locations whose 800-171 program is managed centrally, a reasonable estimate is $15,000-$35,000. That pricing is comparable to an ISO 27002 Gap Assessment, which is a reasonable proxy in terms of size and approach to CMMC Level 3 (130 controls) as ISO 27002 covers 114 controls. Differences between the upper and lower ends of the range have to do with sampling rates and whether technical testing is included in the work effort. If you require support for Gap Remediation that can range considerably based on the findings. In a more mature environment, $0-$10,000 is a reasonable estimate. If you are less mature than you thought, $0-$25,000 is a reasonable estimate. Pro-tip – If you don’t have an up-to-date Risk Assessment and System Security Plan then you don’t have a reasonably mature environment.
- Hard Costs for Prep: If you are reasonably mature you likely will need to spend very little in hard costs to get prepped. It’s entirely reasonable to assume $0. You are not reasonably mature if you have not made notable investments in the last five years for items like endpoint protection, multi-factor authentication, log monitoring/SIEM, etc.
- Hard Costs for Audit: This one is harder to estimate given that there is not yet any guidance for the audit process. If I were designing the audit program I would set it up like the Standardized Control Assessment from Shared Assessments. It is essentially a fully defined audit program including the questions to ask, artifacts to gather, sampling rates and a prescribed reporting format. Assuming the audit program follows a model of this nature the pricing across auditors should be fairly consistent. Best guess: $20,000-$40,000.
- Organizations without a mature SP 800-171 compliant environment
- Consulting Costs: You will likely want to start with a CUI Scoping Exercise (to try to minimize the scope and associated costs) and a Risk Assessment (a requirement of CMMC) first. This will ensure you have the proper context for the Gap Assessment. For a typical 250-person engineering/manufacturing firm with multiple locations a good estimate is $30,000-$50,000. That pricing is comparable to establishing the foundation of an ISO 27001 or SOC 2 information security program, which is a reasonable proxy in terms of size and approach. Differences between the upper and lower ends of the range have to do with current maturity, CUI scope and project approach. If you require support for Gap Remediation that can range considerably based on the findings. In a less mature environment, $10,000-$40,000 is a reasonable estimate. Taking this approach generates the required Risk Assessment and builds the foundational Scope Statement that is integral to the required System Security Plan.
- Hard Costs for Prep: Cost here depends on the technology you have implemented in your environment. CMMC level 3 ostensibly requires mobile device management, log monitoring/SIEM, security awareness training, multifactor authentication, data backups, code review and advanced email protection. Most viable organizations are going to have a fair number of these tools in place. Best case: $0. Typical case: $20,000-$60,000. Worst case: $100,000. As an example, a conversation was recently had with a client at a 100-person firm that has a very mature NIST SP 800-171 compliant environment, which cost approximately $170,000 to achieve from scratch. This is consistent with the ranges floated.
- Hard Costs for Audit: As above, best guess: $20,000-$40,000.
Summary
The takeaway here is that the organization seeking CCMC certification needs to:
- Conduct or have an assessment completed using NIST 800-171 guidelines. This will establish a cyber security baseline and give the organization an idea of what it needs to do and/or how much it may need to budget for various level certifications.
- Work with an ETHICAL, independent assessor that understands it will need to complete training/examination and work with an approved C3PAO. In 21CT’s case this will be its relationship with ACS/Canon and its own independent certification to be achieved in 3Q 2020.
- Be patient. The CMMC is an evolving process. The first Request For Information (RFI) is not due to the CMMC hierarchy until June 12, 2020 so the groups responsible for providing training, conducting examinations and providing the actual CMMC certifications to assessors is not completed. This is all a work in progress.