Cybersecurity Maturity Model Certification (CMMC) Primer and Estimated Costs

CMMC (Cybersecurity Maturity Model Certification) is the Department of Defense’s (DoD) newest verification mechanism designed to ensure that cybersecurity controls and processes adequately protect Controlled Unclassified Information (CUI) that resides on Defense Industrial Base (DIB) systems and networks.
The Office of the Undersecretary of Defense for Acquisition and Sustainment (OUSD (A&S)) started the process of creating the CMMC in March 2019, the finalization of CMMC v1.0 being issued in January 2020.
The Department of Defense created a requirement for all organizations in the defense supply chain contracting with the government to achieve the appropriate level of Cybersecurity Maturity Model Certification. Organizations in the defense supply chain achieve the appropriate CMMC level through assessment by a neutral and properly accredited third party entity. This entity assesses an organization’s cybersecurity maturity against criteria defined in the CMMC standard.
The CMMC-Accreditation Body (CMMC-AB) is responsible for developing a scalable and extensive partner-centric training and educational model to effectively equip professionals, students and other stakeholders within the CMMC ecosystem. The CMMC-AB will, as part of its strategy, certify Licensed Partner Publishers (LPP) to develop learning content and Licensed Training Providers (LTP) to train stakeholders for certification or other purposes.
Individuals seeking certification by CMMC-AB as CMMC Certified Professionals (CP) or Certified Assessors (CA) must successfully complete a training program delivered by a LTP and pass a proctored examination prior to receiving certification to prepare for or conduct assessments. The CMMC-AB will license/accredit assessors to perform formal assessments under the CMMC once they satisfactorily complete the training, examination and certification requirements.
Assessors will affiliate with CMMC Third Party Assessment Organizations (C3PAOs). The C3PAOs serve as the interface between the Organizations Seeking Certification (OSCs), the Assessment and the CMMC-AB.
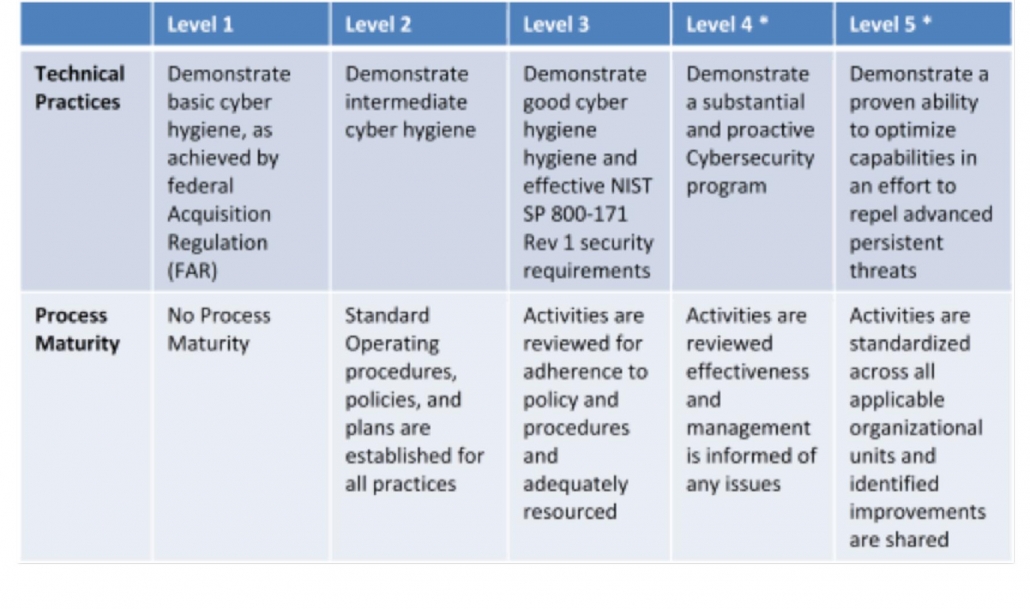
CMMC has five levels of certification. 17 domains are assessed even at the most basic level.
Each level of CMMC maturity has increasing expectations:
- CMMC Level 1: 17 Controls.
- CMMC Level 2: 72 Controls (includes Level 1 controls)
- CMMC Level 3: 130 Controls (includes Level 2 controls)
- CMMC Level 4: 156 Controls (includes Level 3 controls)
- CMMC Level 5: 171 Controls (includes Level 4 controls)
How Much Will CMMC Certification Cost?
For most organizations there are likely to be three primary costs to getting CMMC certified:
- Soft costs to prepare for the audit (e.g., internal resourcing or external consulting costs)
- Hard costs to prepare for the audit (e.g., expenditures to achieve a particular requirement such as a SIEM or two-factor authentication)
- Hard costs for the CMMC Audit itself (e.g., the cost for the Certified Auditor, which potentially will be an “allowable expense”)
Soft costs for getting prepared for the audit
Your actual costs will depend on a number of factors, including but not limited to the maturity of your current NIST SP 800-171 program, the size of your organization, whether you require external support, how many locations are involved, the CMMC Level you’re looking to achieve and the scope of your Controlled Unclassified Information (CUI). CUI scope is how many geographic locations, systems, databases, applications and networks store, process or transit CUI. To simplify, let’s break the above into two buckets and assume CMMC Level 3, which is likely to be the most common target:
Summary
The takeaway here is that the organization seeking CCMC certification needs to:
- Conduct or have an assessment completed using NIST 800-171 guidelines. This will establish a cyber security baseline and give the organization an idea of what it needs to do and/or how much it may need to budget for various level certifications.
- Work with an ETHICAL, independent assessor that understands it will need to complete training/examination and work with an approved C3PAO. In 21CT’s case this will be its relationship with ACS/Canon and its own independent certification.
- Be patient. The CMMC is an evolving process. This is all a work in progress.